Every year, the amount of e-waste that is recorded is rising rapidly. With the constant and rapid advances in technologies, there is a constant consumer demand for the latest leading mobile phones, laptops, computers, and any other form of electronic devices. With a constant ‘out with the old’ and ‘in with the new’ consumer culture, the rise in the level of e-waste looks set to continue. In 2018, there was approximately 50 million tonnes of e-waste produced worldwide. Of this, it is estimated that only 12.5% of it is actually recycled, so there is a huge scope for growth.
So, what is urban mining and how does it come in to play? Well, it is estimated that there is around 40 to 50 times more gold and other precious metals within e-waste products such as mobile phones, computers and other forms of electronics than what there is the traditionally ore mining areas.
In addition to this, extracting precious metals from e-waste is said to cost over 13 times more than what it costs to extract them from traditional mining ore methods.
So, this is where the practice of urban mining comes in. Firstly, urban mining involves the recovery of electronic e-waste. Once collected it is then transported to a recycling depot in the same sense as what happens to any other recyclable product. The e-waste is then sorted into product categories and once this has been done, the e-waste is sent to an urban mining plant where a chemical engineering process recover the metals from the e-waste.
There are already concerns about the depleting available supply of certain minerals. Gold, silver, cobalt, rhodium, indium and zinc have all been put on a shortlist of some of the minerals that are believed to be unavailable to mine in the next 15 to 20 years, thus highlighting the need for a far more advanced urban mining system.
There are over 60 elements within mobiles alone, all containing high levels of gold, silver, palladium, platinum, indium, copper, nickel, tin and tantalum – all of which can be extracted from mobile e-waste. Consumer demand for products ever increasing within a world where resources are becoming depleted, one thing is for sure – the need for urban mining is only ever going to increase.

What is a Blockchain?
A blockchain is a process which creates a decentralized chain of information that flows from one entity to another. It cuts out the middleman and by doing this, it carries no transaction cost outside of it’s initial infrastructure cost. The blockchain is a simple yet highly ingenious way of transferring information from A to B in a fully automated, safe and secure manner. One party to a transaction initiates the process by creating a block. This block is verified by thousands, perhaps millions of computers distributed around the net. The verified block is added to a chain, which is stored across the net, creating not just a unique record, but a unique record with a unique history. Falsifying a single record would mean falsifying the entire chain in millions of instances, which is virtually impossible to do.
Think of a railway company. When we buy tickets on an app or on the internet, the credit card company takes a cut for processing the transaction. With blockchain, not only can the railway operator save on credit card processing fees, it can move the entire ticketing process to the blockchain. The two parties in the transaction are the railway company and the passenger. The ticket is a block, which will be added to a ticket blockchain. Just as a monetary transaction on blockchain is a unique, independently verifiable and unfalsifiable record (like Bitcoin), so can your ticket be. Incidentally, the final ticket blockchain is also a record of all transactions for, say, a certain train route, or even the entire train network, comprising every ticket ever sold, every journey ever taken.
But the key here is this: it’s free. Not only can the blockchain transfer and store money, but it can also replace all processes and business models which rely on charging a small fee for a transaction, or any other transaction between two parties.
The Three Pillars of Blockchain Technology
Decentralization, transparency and immutability are the three main properties of Blockchain Technology that are propelling this new technology to revolutionary status, and are driving blockchain technology to represent the rebirth of the internet as we have come to know it.
Pillar 1: Decentralization
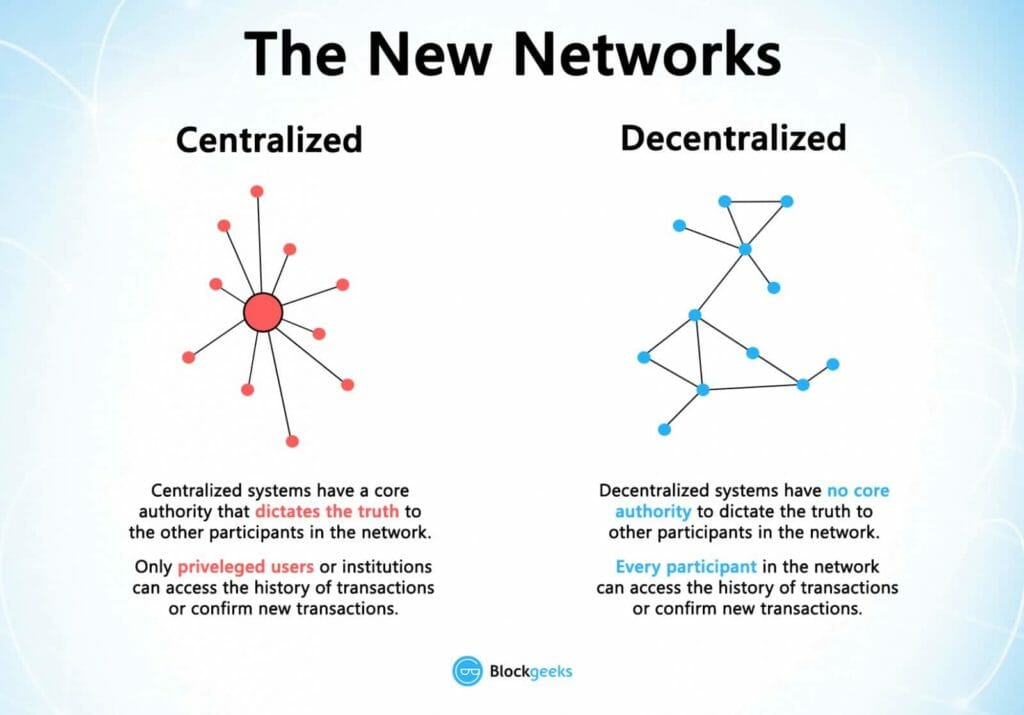
Before Bitcoin and BitTorrent came along, we were more used to centralized services. The idea is very simple. You have a centralized entity which stored all the data and you’d have to interact solely with this entity to get whatever information you required.
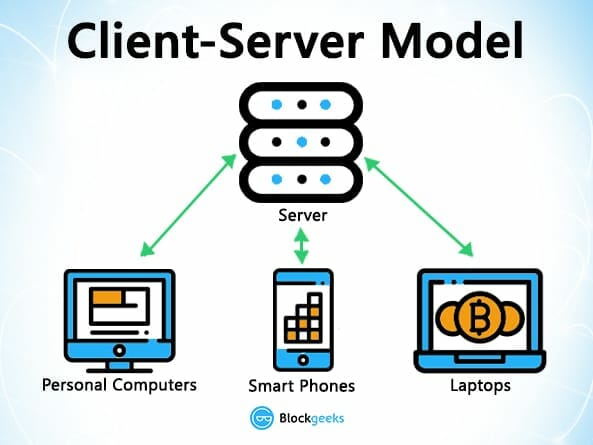
For instance, when you carry out a search on google, or any other internet search engine, you simply send a query to the server who then gets back to you with the relevant information that you’ve requested. This is centralized system which is controlled by a simple client-server.
Another example of a centralized system is banks. They store all of your money, and the only way that you can transact a payment to someone is by going through the bank.
The traditional client-server model is a perfect example of this:
It is fair to say that centralized systems have been extremely useful to us for many years, but it is inescapable to not see that they have several vulnerabilities. Firstly, because they are centralized, all the data is stored in one spot. This makes them easy target spots for potential hackers. If the centralized system were to go through a software upgrade, it would halt the entire system.
What if the centralized entity somehow shut down for whatever reason? That way nobody will be able to access the information that it possesses
Worst case scenario, what if this entity gets corrupted and malicious? If that happens then all the data that is inside the blockchain will be compromised.
So, what happens if we just take this centralized entity away?
In a decentralized system, the information is not stored by one single entity. In fact, everyone in the network owns the information.
In a decentralized network, if you wanted to interact with your friend then you can do so directly without going through a third party. That was the main ideology behind Bitcoins. You and only you alone are in charge of your money. You can send your money to anyone you want without having to go through a bank.
Pillar 2: Transparency
One of the most interesting and misunderstood concepts in blockchain technology is “transparency.” Some people say that blockchain gives you privacy while some say that it is transparent.
Well… a person’s identity is hidden via complex cryptography and represented only by their public address. So, if you were to look up a person’s transaction history, you will not see “Bob sent 1 BTC” instead you will see “1TQ1bdwrTLkVsgs6vpFYIxc3TnTvyCq2GHW sent 1 BTC”. It is the same for any transaction, making our payment history far more private to the eyes of millions of people who work at the companies who we do business with, thus enhancing our privacy and the security of our data footprints. The following snapshot of Ethereum transactions will show you what we mean:
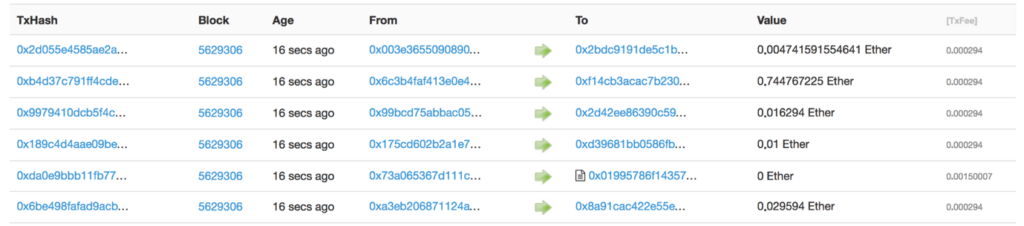
So, while the person’s real identity is secure, you will still see all the transactions that were done by their public address. This level of transparency has never existed before within a financial system. It adds that extra, and much needed, level of accountability which is required by some of these biggest institutions.
Pillar 3: Immutability
In the context of blockchain, it’s immutability means that once something has been entered into the blockchain process, no information whatsoever is capable of being altered, tampered with or deleted.
Can you imagine how valuable this will be for financial institutes?
Imagine how many embezzlement cases can be nipped in the bud if people know that they can’t “cook the books” and get creative when filing their company accounts.
The reason why the blockchain possesses this characteristic is because of the cryptographic hash function.
To put things simply, hashing means taking an input string of any length and giving out an output of a fixed length. In the context of cryptocurrencies like bitcoin, the transactions are taken as an input and run through a hashing algorithm (bitcoin uses SHA-256) which gives an output of a fixed length.
Let’s see how the hashing process works. We are going to put in certain inputs. For this exercise, we are going to use the SHA-256 (Secure Hashing Algorithm 256).

As you can see, in the case of SHA-256, no matter how big or small your input is, the output will always have a fixed 256-bits length. This becomes critical when you are dealing with a huge amount of data and transactions. So basically, instead of remembering the input data which could be huge, you can just remember the hash and keep track.
A cryptographic hash function is a special class of hash functions which has various properties making it ideal for cryptography. There are certain properties that a cryptographic hash function needs to have in order to be considered secure.
There is just one property that we want you to focus on today. It is called the “Avalanche Effect.”
Even if you make a small change in your input, the changes that will be reflected in the hash will be huge. Let’s test it out using SHA-256:

We can clearly see that even though we have simply just changed the case of the first letter of the input, the output of the entire hash has significantly changed it’s appearance.
The blockchain is a linked list which contains data and a hash pointer which points to its previous block, hence creating the chain. A hash pointer is similar to a pointer, but instead of just containing the address of the previous block it also contains the hash of the data inside the previous block.
This one small tweak is what makes blockchains so amazingly reliable and trailblazing.
Imagine this for an example – a hacker attacks block 4 and tries to change the data. Due to the properties of hash functions, we know that a slight change in data will dramatically change the hash. This means that any slight changes made in block 4, will change the hash which is stored in block 3. This will in turn change the data and the hash of block 3 which will result in changes in blocks 2 and 1, and so on and so forth, depending upon which block within the chain that a hacker tries to manipulate. This will completely change the chain, which is impossible, and this is exactly how blockchains attain complete immutability.
